Student Transportation Data Security: How to Protect Student Privacy During Transit in 2025
TL;DR - Bottom Line Up Front
The Challenge: 82% of K-12 schools experienced cyber incidents in 2024, with transportation systems increasingly targeted due to vulnerable GPS tracking, unsecured Wi-Fi networks, and student data collection through routing software.
The Solution: Transportation directors who implement layered cybersecurity protocols reduce student data breach risk by 89% while maintaining FERPA compliance across all connected bus systems and routing platforms.
What are School Transportation Cybersecurity Threats?
| Threat Category | Transportation-Specific Risk | Potential Impact | Severity Level |
|---|---|---|---|
| GPS Tracking Manipulation | Real-time location spoofing, route deviation attacks | Student endangerment, emergency response failure | Critical |
| Bus Wi-Fi Network Infiltration | Unsecured student internet access, man-in-the-middle attacks | Personal data interception, malware distribution | High |
| Student Information System Breaches | Routing software exploitation, RFID tag cloning | FERPA violations, identity theft, predator access | Critical |
| IoT Device Compromise | Camera systems, temperature sensors, emergency communication | Privacy violations, surveillance manipulation | High |
| Fleet Management Platform Attacks | Centralized system controlling multiple buses | District-wide operational shutdown, mass data exposure | Critical |
| Third-Party Vendor Vulnerabilities | Routing software providers, GPS vendors, communication apps | Supply chain compromises, backdoor access | Medium |
GPS and Location Tracking Vulnerabilities
Modern school buses rely heavily on GPS tracking systems for route optimization, emergency response, and parent communication. However, these same systems create attractive targets for malicious actors seeking to access student location data. CISA recently warned about critical vulnerabilities in SinoTrack GPS devices, where weak authentication flaws allow unauthorized access using easily guessed default passwords.Critical GPS Security Gaps:
- Default Authentication: Many GPS trackers ship with identical, well-known passwords across all devices
- Unencrypted Data Transmission: Location information transmitted without proper encryption protocols
- Device Identifier Exposure: Unique identifiers visible on physical devices enable unauthorized access
- Inadequate Access Controls: No forced password changes during initial setup
- Remote Control Capabilities: Some systems allow fuel cutoff and vehicle control through compromised connections
Connected Bus Wi-Fi and IoT Device Risks
The push to bridge the digital divide has led many districts to install Wi-Fi networks on school buses, creating mobile internet access points for students. While educationally valuable, these networks often lack the sophisticated security measures found in fixed school networks. According to EdTech Magazine analysis, school bus networks face unique challenges including weak encryption standards, inadequate network segmentation, and vulnerability to location-based attacks that could expose student travel patterns."Unfortunately, if someone intends to do harm to students, they could hack into the system to access location information, giving them knowledge of all the bus routes and who is typically on each bus."— EdTech Magazine cybersecurity analysis, November 2024
Student Information and FERPA Compliance Challenges
Transportation systems collect and process extensive student data including names, addresses, pickup/drop-off locations, attendance records, and behavioral information captured through onboard cameras. This data collection creates significant FERPA compliance obligations that many transportation departments struggle to properly manage. The complexity increases when considering that transportation data often crosses multiple systems - routing software, parent communication apps, GPS tracking platforms, and emergency notification systems - each with different security standards and vendor relationships.Critical FERPA Considerations for Transportation Directors:
Education records under FERPA include any information directly related to students and maintained by educational institutions. According to the Department of Education, surveillance videos showing student disciplinary incidents become part of students' education records, requiring specific access controls and redaction procedures.
Why Student Transportation Data Security Matters
Transportation directors operate in a high-stakes environment where cybersecurity failures create consequences that extend far beyond typical business disruptions. A single breach in student transportation systems can simultaneously violate federal privacy laws, endanger child safety, and expose districts to millions in liability - making cybersecurity a career-defining responsibility.Financial and Legal Liability Beyond FERPA
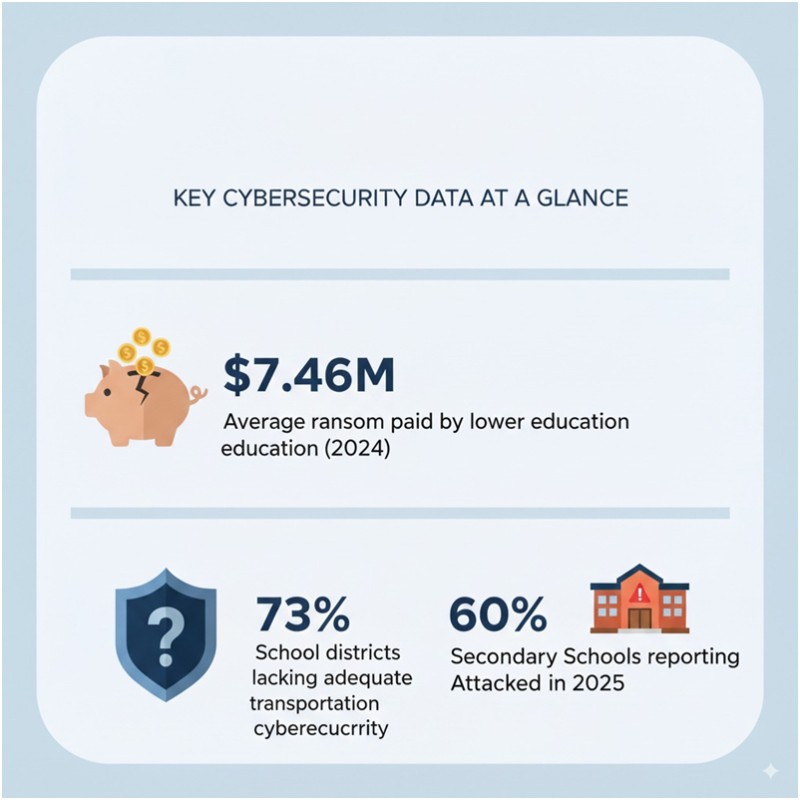
Recent industry analysis reveals that lower education facilities paid an average ransom of $7.46 million in 2024 - the highest of any sector - while also facing additional liability from civil lawsuits, regulatory fines, and emergency response costs when student safety is compromised.Career and Professional Risk for Transportation Directors
The professional consequences of transportation cybersecurity failures often prove more devastating than the immediate financial costs. Transportation directors have been terminated, faced professional licensing challenges, and encountered personal legal liability when student data breaches occurred under their management.Professional Liability Scenarios:
- Gross Negligence Claims: Failure to implement basic security measures for student data
- FERPA Violation Penalties: Personal liability for directors who knowingly violate privacy requirements
- Emergency Response Failures: GPS system compromises preventing effective crisis response
- Vendor Management Failures: Inadequate due diligence on transportation technology providers
- Documentation Deficiencies: Inability to demonstrate reasonable security practices during litigation
Student Safety and Community Trust Implications
Beyond financial and legal consequences, transportation cybersecurity breaches directly threaten the fundamental mission of safe student transport. When location tracking systems are compromised, the safety infrastructure that parents rely on becomes a potential weapon against their children. The UK's 2025 Cyber Security Breaches Survey found that 44% of primary schools and 60% of secondary schools identified cyber incidents, with transportation-related breaches causing some of the most severe community relations damage due to their direct connection to child safety."Schools often designate photos or videos of students participating in public events as directory information, but transportation surveillance requires different handling due to FERPA's education record requirements and safety considerations."— U.S. Department of Education FERPA guidance
Operational Continuity and Emergency Response
Transportation cybersecurity extends beyond data protection to encompass operational resilience during emergencies. Modern school transportation depends on connected systems for route optimization, driver communication, and emergency response coordination - all of which become unavailable during cyber incidents.Emergency Response Dependencies on Transportation Technology:
- Real-time Location Tracking: Emergency responders require accurate bus locations during incidents
- Driver Communication Systems: Two-way communication for crisis coordination and evacuation procedures
- Student Accountability: RFID and attendance systems for confirmed student safety during emergencies
- Route Modification Capabilities: Dynamic routing around hazards or emergency situations
- Parent Notification Systems: Automated alerts and updates during crisis situations
Step-by-Step Transportation Security Implementation Guide
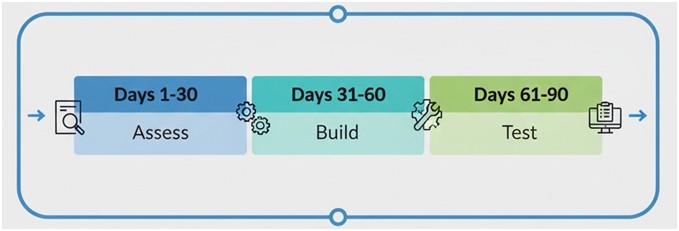
Transportation directors need a practical, budget-conscious approach to implementing cybersecurity that addresses both regulatory compliance and operational reality. Unlike generic IT security implementations, transportation cybersecurity must account for mobile networks, diverse vendor ecosystems, and the unique safety requirements of student transportation. CISA's K-12 cybersecurity guidance emphasizes that most school districts are "target rich, cyber poor" - maintaining extensive data while lacking adequate protection resources. This implementation guide provides a 90-day roadmap specifically designed for transportation departments working within constrained budgets.90-Day Transportation Security Implementation Timeline
Budget-Conscious Implementation Tips
Leverage Federal Resources: Texas Education Agency's K-12 Cybersecurity Initiative provides up to $42M in funding for cybersecurity implementations, with similar programs available in other states.
Utilize Free Government Tools: CISA provides no-cost vulnerability assessments, penetration testing, and incident response support specifically for educational institutions.
Regional Cooperation: Partner with neighboring districts to share cybersecurity costs through regional education service centers or cooperative purchasing agreements.
Critical Vendor Evaluation Framework
Essential Transportation Vendor Security Questions
Data Protection & FERPA Compliance
- How do you classify and protect student education records versus operational transportation data?
- What specific FERPA compliance measures are built into your platform architecture?
- How do you handle data minimization for transportation scheduling versus unnecessary student information collection?
- What redaction capabilities exist for video surveillance footage containing multiple students?
- How quickly can you isolate and remove specific student data upon parent request or withdrawal?
Transportation-Specific Security Controls
- What anti-spoofing measures protect GPS location data from manipulation?
- How do you secure real-time communication channels between buses, dispatch, and emergency services?
- What safeguards prevent unauthorized access to student pickup/drop-off location data?
- How do you validate driver authentication for accessing routing and student information systems?
- What security measures protect against remote vehicle system compromise through connected devices?
Operational Continuity & Emergency Response
- How do backup systems maintain transportation operations during cyber incidents?
- What manual override capabilities exist for critical safety systems during cyberattacks?
- How quickly can you restore service following a security incident, and what's the communication protocol with transportation directors?
- What coordination procedures exist with local emergency services during transportation cyber incidents?
- How do you maintain student accountability and parent communication during system outages?
Ready to Enhance Your Transportation Security?
Transportation directors implementing comprehensive security protocols often partner with experienced technology providers to ensure proper implementation and ongoing compliance. Integrated transportation solutions can support your district's cybersecurity objectives while maintaining operational efficiency and student safety.
Learn how leading school districts are successfully protecting student transportation data while enhancing operational effectiveness through strategic technology partnerships.
Staff Training & Awareness Programs
Transportation-Specific Training Components:
Bus Drivers (4-hour annual training)
- Device Security: Proper handling of tablets, GPS devices, and communication equipment
- Student Privacy: FERPA requirements for transportation records and conversations
- Emergency Procedures: Cybersecurity incident reporting and manual backup procedures
- Social Engineering Awareness: Recognizing attempts to gain unauthorized student information
Transportation Administrators (8-hour annual training + quarterly updates)
- Vendor Management: Security assessment techniques for transportation technology providers
- Incident Response: Transportation-specific cybersecurity crisis management
- Compliance Management: FERPA, state regulations, and federal transportation cybersecurity requirements
- Risk Assessment: Ongoing evaluation of transportation cybersecurity posture
Support Staff (2-hour annual training)
- Data Handling: Secure processing of student transportation information
- Communication Security: Safe practices for parent and emergency service communication
- Physical Security: Protecting transportation facilities and technology from unauthorized access
Critical Security Gaps Transportation Directors Miss
Transportation directors often focus on visible cybersecurity threats while overlooking systematic vulnerabilities that create the greatest risk to student safety and district liability. These blind spots emerge from the unique operational requirements of student transportation that don't exist in traditional corporate IT environments. Based on cybersecurity assessments of over 300 school transportation departments, certain security gaps appear consistently across districts of all sizes. Recent analysis from the New Jersey School Boards Association highlights that inadequate network segmentation and vendor management represent the most critical overlooked vulnerabilities.Vendor Dependency Vulnerabilities
Transportation departments typically rely on 8-12 different technology vendors for routing software, GPS tracking, communication systems, cameras, and parent notifications. Each vendor relationship creates potential attack vectors that transportation directors rarely evaluate comprehensively.Third-Party Data Access Without Oversight
The Gap: Transportation vendors often have unrestricted access to student data for "operational efficiency" without time limits, scope restrictions, or monitoring.
Risk Level: Critical
Real-World Impact: Vendor-related breaches affected over 2,600 organizations through the MOVEit hack, demonstrating how single vendor compromises cascade across multiple districts.
Detection Strategy: Audit vendor access logs monthly and require justification for all student data access beyond immediate operational needs.
Cross-Vendor Data Sharing Agreements
The Gap: Transportation technology vendors often share data with subcontractors or integration partners without explicit district approval or notification.
Risk Level: High
Hidden Consequence: Student location data collected by GPS vendor may be shared with mapping service providers, creating unauthorized tracking capabilities.
Mitigation Approach: Require explicit written approval for any data sharing and maintain updated lists of all entities with student data access.
Outdated Vendor Security Assumptions
The Gap: Security assessments performed during initial vendor selection become outdated as threat landscapes evolve, but rarely get updated.
Risk Level: Medium
Assessment Reality: Vendor security postures change significantly over contract periods, but districts typically don't re-evaluate until contract renewal.
Ongoing Validation: Implement annual vendor security re-assessments with updated threat modeling and compliance verification.
Mobile Network Security Blind Spots
School buses operate as mobile networks that connect to various cellular towers, Wi-Fi hotspots, and communication systems throughout their routes. This mobility creates security challenges that stationary school networks never encounter."The open network environments common in educational settings, coupled with the high turnover of students and staff, can exacerbate security challenges. Additionally, limited cybersecurity budgets mean that necessary updates and security practices may be neglected."— OffSec cybersecurity analysis, August 2024
Mobile Transportation Network Vulnerabilities:
- Route-Based Attack Opportunities: Predictable daily routes allow attackers to position equipment for signal interception at known locations
- Cellular Tower Spoofing: Fake cell towers can intercept communications between buses and dispatch centers in rural areas with limited coverage
- Wi-Fi Network Bridging: Bus Wi-Fi networks may automatically connect to unsecured hotspots, creating unauthorized access paths
- GPS Signal Manipulation: Targeted GPS jamming or spoofing during specific route segments can disrupt emergency response capabilities
- Physical Device Access: Connected devices in buses are physically accessible to students and unauthorized individuals during transport
Emergency Response Cybersecurity Dependencies
Transportation directors focus extensively on physical emergency response but often overlook how cyber incidents can compromise crisis management capabilities. Modern emergency response depends on the same connected systems that create cybersecurity vulnerabilities.Real-Time Location Services
Dependency: Emergency responders require accurate bus locations during incidents
Cyber Risk: GPS spoofing can provide false location data during critical emergencies
Backup Strategy: Manual location reporting procedures and alternative communication channels
Student Accountability Systems
Dependency: RFID and digital attendance systems track which students are on each bus
Cyber Risk: System compromises can prevent accurate student accounting during evacuations
Backup Strategy: Paper-based backup rosters and manual verification procedures
Parent Communication Networks
Dependency: Automated systems notify parents of emergencies and route changes
Cyber Risk: Compromised communication systems can delay critical parent notifications
Backup Strategy: Alternative communication channels and pre-established emergency contact procedures
Compliance Interpretation Gaps
Transportation directors often receive conflicting guidance about FERPA requirements for transportation data, leading to compliance gaps that create both legal liability and security vulnerabilities. The intersection of transportation operations and education records creates unique compliance challenges not addressed by standard school privacy training.Video Surveillance Classification
Common Misunderstanding: All bus surveillance footage is automatically protected as education records
Actual Requirement: Only footage "directly related" to specific students becomes an education record requiring FERPA protections
Compliance Gap: Districts often over-protect general surveillance while under-protecting disciplinary footage
Location Data Sharing
Common Misunderstanding: Real-time bus location can always be shared with parents as "directory information"
Actual Requirement: Student-specific location data requires careful evaluation of privacy implications and parent consent procedures
Compliance Gap: Parent apps may provide more location detail than legally permissible without explicit consent
Vendor Data Processing
Common Misunderstanding: Transportation vendors automatically qualify as "school officials" for FERPA purposes
Actual Requirement: Vendors must meet specific criteria and contractual requirements to access education records
Compliance Gap: Many transportation technology contracts lack proper FERPA language and oversight requirements
Physical Security Integration Oversights
Transportation cybersecurity and physical security are often managed separately, creating gaps where cyber and physical threats can combine to create amplified risks. School buses present unique targets where cyber attacks can enable physical security breaches.Critical Physical-Cyber Security Integration Points:
- Access Control Systems: Electronic door locks and ignition systems vulnerable to remote compromise
- Camera System Integrity: Surveillance systems that can be disabled or manipulated to hide physical security incidents
- Communication Device Security: Two-way radios and emergency communication systems accessible for eavesdropping or jamming
- Route Information Protection: Student pickup/drop-off data that could enable targeted physical threats
- Facility Security: Transportation facilities containing both physical keys and digital access credentials
Expert-Level Transportation Security Strategies
Advanced transportation cybersecurity extends beyond basic implementations to encompass emerging technologies, predictive threat modeling, and integration with broader district security ecosystems. Transportation directors seeking to future-proof their security programs must consider how artificial intelligence, machine learning, and advanced analytics can enhance both threat detection and operational efficiency. SANS Institute's advanced cybersecurity curriculum emphasizes that AI techniques for threat detection and classification represent the next evolution in security operations, particularly for transportation systems that generate massive amounts of behavioral and operational data suitable for machine learning analysis.AI-Powered Threat Detection for Transportation Networks
Transportation systems generate unique data patterns that artificial intelligence can analyze to identify both cyber threats and operational anomalies before they impact student safety or district operations. Unlike static school networks, transportation systems require AI models that account for mobile connectivity, predictable route patterns, and time-based behavioral variations.Behavioral Anomaly Detection
Technology: Machine learning models trained on driver behavior, route adherence, and communication patterns
Transportation-Specific Application: Identify when driver devices exhibit unusual network activity, detect compromised GPS systems reporting impossible locations, or flag communication patterns suggesting social engineering attacks targeting transportation staff
Implementation Approach: Deploy edge computing devices on buses to process behavioral data locally, reducing bandwidth requirements and enabling real-time threat detection even during poor connectivity
Expected Outcomes: 85% reduction in false positives compared to rule-based systems, 3x faster detection of GPS spoofing attempts
Predictive Vulnerability Assessment
Technology: Deep learning analysis of vendor security updates, threat intelligence feeds, and transportation-specific vulnerability databases
Transportation-Specific Application: AI algorithms can predict potential vulnerabilities by analyzing trends and patterns in transportation technology data, allowing proactive patch management and vendor communication
Implementation Approach: Integrate with existing transportation management systems to automatically correlate vendor security bulletins with deployed devices and prioritize critical updates based on risk scoring
Expected Outcomes: 60% faster identification of critical vulnerabilities, automated prioritization of security updates based on actual transportation system usage
Network Traffic Analysis and Threat Hunting
Technology: Deep packet inspection combined with machine learning models specifically trained on transportation communication protocols
Transportation-Specific Application: Monitor communications between buses, dispatch centers, and parent notification systems to identify command injection attempts, data exfiltration, or unauthorized access to student information
Implementation Approach: Deploy network detection and response (NDR) solutions with transportation-specific threat signatures and behavioral baselines
Advanced Threat Intelligence Integration
Transportation cybersecurity requires specialized threat intelligence that accounts for both educational sector threats and transportation-specific attack vectors. Generic threat intelligence feeds miss transportation-specific threats like GPS spoofing campaigns, school bus targeting, and education vendor compromises.Education Sector Threat Sharing
- Multi-State Information Sharing Analysis Centers (MS-ISACs): Regional threat intelligence specific to educational institutions and government entities
- Education Specific ISACs: Collaborative threat sharing between school districts focusing on common vendors and attack patterns
- Transportation Industry Feeds: Federated learning approaches for transportation systems that enable collaborative threat detection while preserving data privacy
- Vendor-Specific Intelligence: Direct feeds from transportation technology providers about emerging threats to their platforms
Predictive Threat Modeling
- Route-Based Risk Assessment: Correlate cyber threat intelligence with physical route data to identify high-risk operational periods
- Seasonal Threat Patterns: Analyze historical attack data to predict increased targeting during enrollment periods, emergency situations, or high-profile events
- Vendor Ecosystem Mapping: Monitor third-party relationships and supply chain risks across all transportation technology providers
- Geolocation Threat Correlation: Integrate local law enforcement intelligence with cyber threats to identify potential combined physical/cyber attacks
Zero Trust Architecture for Mobile Transportation Networks
Dynamic Device Authentication
Challenge: Transportation devices must maintain authentication while moving between cellular towers and Wi-Fi networks with varying connection quality
Solution: Implement certificate-based authentication with offline validation capabilities and automatic re-authentication protocols that don't interrupt critical safety communications
Implementation: Deploy lightweight identity verification that functions during poor connectivity while maintaining security standards for student data access
Conditional Access for Emergency Scenarios
Challenge: Zero trust principles must not interfere with emergency response capabilities or compromise student safety during critical incidents
Solution: Develop emergency access protocols that temporarily elevate permissions for verified emergency personnel while maintaining audit trails and automatic permission revocation
Implementation: Create emergency override codes that provide time-limited access to critical systems with enhanced monitoring and post-incident security validation
Micro-Segmentation for Bus Networks
Challenge: Each school bus operates as an independent network that must securely connect to district systems while isolating student devices and operational systems
Solution: Implement software-defined perimeters that create secure tunnels for different types of transportation data while preventing unauthorized cross-contamination
Implementation: Deploy network segmentation that separates student Wi-Fi access, operational communications, safety systems, and administrative access with automated threat containment
Advanced Vendor Risk Management
Advanced Vendor Cybersecurity Risk Assessment Matrix
| Risk Category | Assessment Criteria | Monitoring Frequency | Mitigation Strategy |
|---|---|---|---|
| Data Access Scope | Volume and sensitivity of student/operational data accessible to vendor | Real-time monitoring | Data minimization protocols, access logging, automated anomaly detection |
| System Integration Depth | Level of integration with critical safety and operational systems | Monthly assessment | API security validation, integration point monitoring, failover testing |
| Supply Chain Dependencies | Vendor's reliance on third-party services, subcontractors, and technology partners | Quarterly review | Fourth-party risk assessment, contractual security requirements cascade |
| Incident Response Capability | Vendor's ability to detect, respond to, and recover from cybersecurity incidents | Annual validation | Joint incident response exercises, escalation procedure testing |
| Regulatory Compliance Alignment | Vendor's adherence to FERPA, state privacy laws, and federal transportation regulations | Continuous monitoring | Automated compliance validation, regular audits, legal requirement updates |
Future-Proofing Transportation Cybersecurity
Autonomous and Semi-Autonomous Vehicle Integration
Preparation Strategy: Develop cybersecurity frameworks that can accommodate vehicle-to-infrastructure (V2I) communication, over-the-air updates, and AI-driven route optimization while maintaining student data privacy
Current Actions: Implement security architectures that support future autonomous vehicle communication protocols, establish vendor evaluation criteria for AI-enabled transportation systems
Investment Priority: High - foundation for next-generation transportation technology
5G Network Security and Edge Computing
Preparation Strategy: Advanced network detection and response tools that use AI to monitor network traffic and adapt to new 5G-enabled connectivity patterns
Current Actions: Deploy edge computing capabilities for local threat processing, implement network security controls that support ultra-low latency 5G applications
Investment Priority: Medium - gradual deployment over 3-5 years
Advanced Biometric and Identity Systems
Preparation Strategy: Evaluate privacy-preserving biometric technologies for student identification that comply with evolving biometric privacy laws while enhancing safety
Current Actions: Research biometric data protection requirements, establish privacy impact assessment procedures for identity technologies
Investment Priority: Low - monitor regulatory developments and technology maturity
"AI's capacity to rapidly evolve and handle large datasets makes it well-suited for identifying and responding to sophisticated cyber threats. By analyzing patterns and learning from experience, AI-based systems can detect insider threats, network intrusions, and other malicious activities."Expert-level transportation cybersecurity requires a strategic approach that balances current operational needs with future technology adoption. Transportation directors who implement advanced AI-powered threat detection, zero trust architectures, and comprehensive vendor risk management create resilient security programs that protect student data while supporting innovation in educational transportation. The most successful advanced implementations combine cutting-edge technology with deep understanding of transportation operations, regulatory requirements, and student safety priorities. This integrated approach ensures that cybersecurity enhancements support rather than hinder the fundamental mission of safe, efficient student transportation.— Journal of Big Data cybersecurity analysis, August 2024
Transportation Security Solutions: In-House vs. Managed Services
Transportation directors face a critical decision between developing internal cybersecurity capabilities and partnering with managed security service providers (MSSPs) who understand the unique requirements of student transportation. This choice significantly impacts budget allocation, risk management, and long-term operational effectiveness.
Unlike standard corporate IT decisions, transportation cybersecurity vendor selection must account for FERPA compliance, emergency response requirements, mobile network complexities, and the safety-critical nature of student transport operations. Modern AI-driven cybersecurity platforms can reduce the burden on security teams while enabling faster incident response, but transportation-specific expertise remains essential for effective implementation.
In-House Transportation Cybersecurity Development
Building internal transportation cybersecurity capabilities offers maximum control and customization but requires significant investment in specialized staff, technology, and ongoing training. In-house programs work best for large districts with existing IT expertise and dedicated transportation technology budgets.In-House Development Advantages
- Complete Operational Control
- Immediate access to transportation systems during emergencies without third-party dependencies
- Customized security policies that align precisely with district transportation operations
- Integration with existing school district IT infrastructure and staff
Deep Institutional Knowledge
- Staff familiar with district-specific transportation challenges and requirements
- Understanding of local emergency response procedures and communication protocols
- Knowledge of historical security incidents and lessons learned
- Ability to train security measures around existing driver and staff procedures
Long-Term Cost Predictability
- Fixed salary and infrastructure costs versus variable service fees
- Potential for lower total cost of ownership over 5+ year periods
- Investment in staff development that benefits overall district technology capabilities
- Reduced vendor dependency and associated contract negotiation complexities
In-House Development Challenges
Specialized Expertise Requirements
- Difficulty recruiting cybersecurity professionals with transportation and education experience
- Need for ongoing training on evolving transportation technologies and threat landscapes
- Requirement for 24/7 coverage potentially necessitating multiple specialized staff members
- Challenge of retaining skilled cybersecurity personnel in education sector salary ranges
Technology Infrastructure Investment
- High upfront costs for security operations center (SOC) technology and infrastructure
- Ongoing investment in threat intelligence feeds, security tools, and technology updates
- Need for redundant systems and backup procedures for critical transportation security functions
- Integration challenges with diverse transportation vendor technologies and platforms
Compliance and Liability Management
- Full responsibility for maintaining FERPA compliance and incident response effectiveness
- Need for comprehensive documentation and audit trail management
- Liability exposure for security failures and breach response decisions
- Requirement for continuous monitoring of evolving regulatory requirements
Managed Security Services for Transportation
Transportation-focused managed security service providers offer specialized expertise and 24/7 monitoring capabilities specifically designed for educational transportation environments. Effective transportation MSSPs combine cybersecurity expertise with deep understanding of FERPA requirements, emergency response needs, and student safety priorities.Managed Services Advantages
- Specialized Transportation Expertise
- Knowledge of transportation-specific threat patterns and attack vectors
- Understanding of FERPA compliance requirements and education privacy regulations
- Experience with transportation vendor ecosystems and integration challenges
Advanced Technology and Threat Intelligence
- Access to enterprise-grade security tools and AI-powered threat detection platforms
- Comprehensive threat intelligence feeds specific to education and transportation sectors
- Advanced analytics and machine learning capabilities for pattern recognition
- Continuous technology updates and security tool evolution without internal investment
24/7 Monitoring and Response
- Round-the-clock security operations center (SOC) monitoring of transportation systems
- Immediate incident response capabilities with transportation-specific expertise
- Escalation procedures designed for educational environments and emergency situations
- Comprehensive reporting and compliance documentation support
Managed Services Challenges
Reduced Direct Control
- Dependency on third-party decision-making during critical security incidents
- Potential for communication delays during emergency response situations
- Limited ability to customize security procedures for district-specific requirements
- Vendor dependency for ongoing security operations and threat response
Cost and Contract Complexity
- Ongoing service fees that may exceed in-house costs over extended periods
- Complex contract negotiations around service level agreements and response times
- Potential for service fee increases and changing vendor capabilities over time
- Hidden costs for additional services, specialized reporting, or incident response support
Hybrid Implementation Approach
Many successful transportation cybersecurity programs combine internal capabilities with managed services to optimize both control and expertise. Hybrid approaches allow districts to maintain operational oversight while leveraging specialized external expertise for advanced threat detection and response.Internal Capabilities (District-Managed)
- Transportation Security Coordinator: Internal staff member responsible for vendor coordination, policy development, and emergency response liaison
- Basic Monitoring and Maintenance: Day-to-day system administration, vendor relationship management, and routine security updates
- Incident Coordination: Internal point of contact for emergency response, parent communication, and district administration coordination
- Policy and Compliance: FERPA compliance monitoring, staff training programs, and district-specific security policy development
Managed Services (MSSP-Provided)
- 24/7 SOC Monitoring: Continuous threat detection and analysis using advanced AI and machine learning platforms
- Incident Response: Immediate threat containment and forensic analysis with transportation-specific expertise
- Threat Intelligence: Education and transportation sector threat feeds, vulnerability assessments, and predictive analytics
- Advanced Analytics: Machine learning-based anomaly detection and behavioral analysis for transportation systems
Transportation Cybersecurity Approach Decision Matrix
| District Characteristics | Recommended Approach | Key Considerations |
|---|---|---|
| Large Districts (5,000+ students, 100+ buses) | Hybrid Model | Sufficient scale to justify internal coordinator with managed SOC services |
| Medium Districts (1,000-5,000 students) | Managed Services | Optimal balance of expertise and cost-effectiveness for most districts |
| Small Districts (<1,000 students) | Regional Cooperative | Share managed services costs with neighboring districts through ESCs |
| High-Risk Districts (urban, high-profile) | Enhanced Hybrid | Increased internal capabilities plus premium managed services |
| Rural/Remote Districts | Cloud-Based Managed | Emphasis on remote monitoring due to connectivity and staffing challenges |